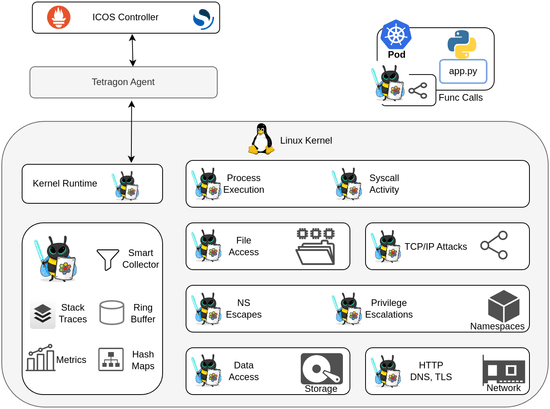
Enhancing Security in the Cloud-Edge-IoT Continuum with ICOS
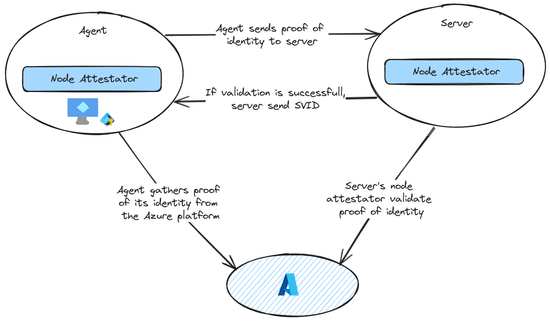
Learn how the ICOS project leverages Cilium and Tetragon to create comprehensive audit reports in its security audit tool
Learn how the ICOS project leverages Cilium and Tetragon to create comprehensive audit reports in its security audit tool
In part 3 of the series, you'll learn how Hubble's rich observability data can be used to enhance your Kubernetes network security posture
In part 2 of the series, you'll learn more about Hubble's powerful observability features and explore how they can enhance your Kubernetes network observability strategy
Explore how Tetragon can be a game-changer for production engineers, particularly when managing incidents and ensuring that SLAs, SLOs, and SLIs are met
Learn about the top security observability use cases for Tetragon
In part 1 of the series, you'll learn about Cilium and Hubble and why they're essential in modern Kubernetes environments
Learn about the top security observability use cases for Tetragon
Explore and try out Cilium's mutual authentication feature
Thomas Graf, co-creator of Cilium, discusses how Cilium fits in the broader networking landscape
For live conversation and quick questions, join the Cilium Slack workspace. Don’t forget to say hi!
Join slack workspace